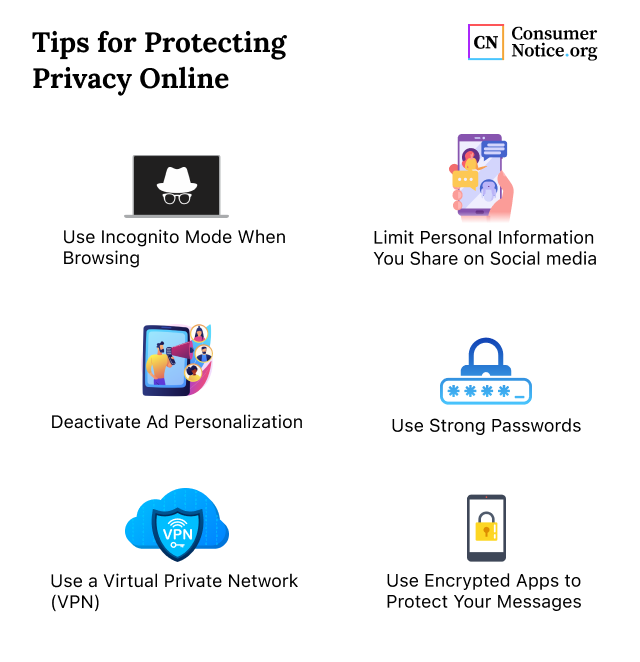
Use strong passwords and enable two-factor authentication to protect your personal data online. Regularly update software and avoid suspicious links.
Protecting your personal data online is essential in today’s digital world. Cyber threats are increasing, making it crucial to secure your information. Simple actions like using strong passwords and enabling two-factor authentication can significantly enhance your online security. Regularly updating software ensures you have the latest security patches.
Avoid clicking on suspicious links to prevent malware attacks. Being cautious with sharing personal information on social media also helps. By following these practices, you can safeguard your personal data from potential threats and maintain your privacy.
Importance Of Personal Data Protection
Protecting your personal data online is crucial in today’s digital age. With the increasing number of cyber threats, understanding the importance of personal data protection can save you from potential risks and damages. Personal data, which includes your name, address, phone number, and financial details, is highly valuable to cybercriminals. Ensuring its safety should be a top priority.
Risks Of Online Data Exposure
Exposing your personal data online can lead to several risks. Cybercriminals are always on the lookout for vulnerabilities to exploit. Here are some common risks:
- Identity Theft: Criminals can use your personal information to impersonate you.
- Financial Fraud: Your banking details can be used to make unauthorized transactions.
- Phishing Attacks: Fake emails can trick you into providing sensitive information.
- Social Engineering: Manipulative tactics can be used to extract personal data.
Understanding these risks can help you take proactive measures to protect your data. Use strong, unique passwords for different accounts and enable two-factor authentication wherever possible. Avoid sharing sensitive information on unsecured websites.
Consequences Of Data Breaches
Data breaches can have severe consequences for individuals and businesses. Here are some potential impacts:
- Financial Loss: Unauthorized transactions can drain your bank account.
- Reputation Damage: Personal information leaks can harm your reputation.
- Legal Issues: You might face legal consequences if your data is misused.
- Emotional Distress: Dealing with identity theft can cause significant stress.
To mitigate these consequences, stay vigilant and monitor your accounts regularly. Report any suspicious activities immediately. Use encryption tools to secure your data and avoid public Wi-Fi for sensitive transactions.
Credit: www.consumernotice.org
Best Practices For Online Data Protection
Protecting your personal data online is crucial in today’s digital age. Cyber threats and data breaches are becoming more frequent. Following best practices for online data protection can help keep your information safe. Below are some essential tips to enhance your online security.
Using Strong And Unique Passwords
Creating strong and unique passwords is one of the most effective ways to protect your personal data. Weak passwords are easy targets for hackers. Follow these tips to create robust passwords:
- Use a mix of uppercase and lowercase letters
- Include numbers and special characters
- Avoid using easily guessable information like birthdays or common words
- Make your password at least 12 characters long
Consider using a password manager to help generate and store unique passwords for each account. This way, you don’t have to remember multiple complex passwords. Password managers also ensure that you don’t reuse passwords across different sites, which is a common security risk.
Here’s a quick comparison of weak vs. strong passwords:
| Weak Password | Strong Password |
|---|---|
| password123 | G@7h&jA!9L#2w |
| qwerty | Hj7^fT@3!kL |
Implementing Two-factor Authentication
Two-Factor Authentication (2FA) adds an extra layer of security to your online accounts. Even if someone gets hold of your password, they will still need the second factor to access your account. Here’s how to set up and use 2FA:
- Go to your account settings.
- Find the security or 2FA section.
- Choose your preferred 2FA method (SMS, email, authentication app).
- Follow the on-screen instructions to complete the setup.
Popular 2FA methods include:
- SMS Authentication: A code is sent to your mobile phone.
- Email Authentication: A code is sent to your email address.
- Authentication Apps: Apps like Google Authenticator generate time-based codes.
2FA significantly reduces the risk of unauthorized access. Always enable 2FA for your most important accounts such as email, banking, and social media. It’s a simple step that provides strong protection against hackers.
Securing Your Devices
Protecting your personal data online is essential in today’s digital world. One of the key steps to safeguarding your information is by securing your devices. This involves ensuring your software is up-to-date and using reliable antivirus and anti-malware programs. Let’s dive into these strategies to keep your data safe.
Updating Software Regularly
Updating your software regularly is crucial for the security of your devices. Software updates often include patches for security vulnerabilities that hackers can exploit. Here’s why you should keep your software up-to-date:
- Security Patches: Updates fix known security issues.
- Improved Performance: Updates often enhance the performance of your devices.
- New Features: Updates can introduce new functionalities that improve user experience.
To ensure your software is always current, follow these steps:
- Enable automatic updates for your operating system.
- Regularly check for updates in your device settings.
- Update all installed applications and programs.
Here’s a simple table to help you keep track of your updates:
| Device | Software | Last Updated |
|---|---|---|
| PC/Laptop | Windows/MacOS | Regularly check and update |
| Smartphone | iOS/Android | Enable auto-updates |
| Tablet | iOS/Android | Enable auto-updates |
Using Antivirus And Anti-malware Programs
Using antivirus and anti-malware programs is essential for protecting your personal data. These programs help detect and remove malicious software that can steal your information. Here’s why these tools are important:
- Real-Time Protection: They offer continuous monitoring against threats.
- Malware Removal: They can remove existing malware from your device.
- Safe Browsing: They provide warnings about unsafe websites.
To maximize your protection, consider these tips:
- Choose a reputable antivirus program.
- Regularly update your antivirus software.
- Schedule regular scans for your device.
Here’s a comparison of popular antivirus programs:
| Antivirus Program | Free Version | Paid Version | Key Features |
|---|---|---|---|
| Norton | No | Yes | Real-time protection, malware removal, safe browsing |
| Avast | Yes | Yes | Real-time protection, malware removal, safe browsing |
| McAfee | No | Yes | Real-time protection, malware removal, safe browsing |
By keeping your software updated and using reliable antivirus programs, you can significantly enhance the security of your personal data online.

Credit: www.passcamp.com
Protecting Your Online Accounts
In today’s digital age, protecting your personal data online is more crucial than ever. One of the most effective ways to safeguard your information is by protecting your online accounts. This involves taking proactive measures to secure your login details, being mindful of the data you share, and staying vigilant against cyber threats.
Being Cautious With Personal Information Sharing
Sharing personal information online can be risky if not done carefully. Always be mindful of the details you disclose on social media, forums, and other online platforms. Here are some tips to keep in mind:
- Never share your passwords or PINs with anyone.
- Use strong, unique passwords for different accounts.
- Avoid sharing sensitive information like your home address, phone number, and financial details.
- Limit the information you post on social media profiles.
Additionally, consider the following table to understand what information is safe to share and what to keep private:
| Safe to Share | Keep Private |
|---|---|
| General interests and hobbies | Full name |
| Non-specific job title | Home address |
| First name | Phone number |
Recognizing Phishing Attempts
Phishing is a common method used by cybercriminals to steal personal information. Recognizing phishing attempts is crucial to protecting your online accounts. Here are some signs to look out for:
- Emails or messages with urgent requests for personal information.
- Unusual sender addresses or domain names.
- Links that lead to suspicious websites or ask for login credentials.
- Attachments that you weren’t expecting, especially from unknown senders.
Follow these steps to safeguard against phishing:
- Always verify the sender’s information before clicking on links or downloading attachments.
- Use anti-phishing software and keep it updated.
- Report phishing attempts to your email provider or relevant authorities.
Remember, staying cautious and informed is your best defense against online threats.
Understanding Data Privacy Policies
Protecting your personal data online is crucial in today’s digital world. Understanding data privacy policies is a key step in safeguarding your information. These policies explain how companies collect, use, and protect your data. Being aware of what you agree to helps you make informed decisions.
Reading And Understanding Privacy Policies
Privacy policies can be lengthy and complex. Reading and understanding them is essential to protect your personal information. Here are some tips to help you:
- Look for key sections such as data collection, data usage, and data sharing.
- Identify what data the company collects. This may include personal details, browsing history, and location data.
- Understand how your data will be used. Companies may use it for marketing, analytics, or improving services.
- Check if your data will be shared with third parties. Some companies share data with advertisers or partners.
- Find out your rights regarding your data. This may include options to access, correct, or delete your data.
Below is a simple table to help you understand what to look for in a privacy policy:
| Section | What to Look For |
|---|---|
| Data Collection | Types of data collected |
| Data Usage | How your data is used |
| Data Sharing | Who your data is shared with |
| User Rights | Options for managing your data |
Managing App Permissions
Apps often request access to various parts of your device. Managing app permissions is crucial for protecting your data. Follow these steps:
- Review permissions before installing an app. Check what the app wants to access.
- Limit permissions to only what is necessary for the app to function.
- Regularly check and update app permissions in your device settings.
- Uninstall apps that request excessive permissions.
- Be cautious with apps from unknown developers. These may pose higher risks.
Here is a simple way to manage app permissions on your device:
- Go to Settings on your device.
- Select Apps or Application Manager.
- Choose an app and tap Permissions.
- Toggle off permissions that are not needed.
Seeking Professional Help
Protecting your personal data online is crucial in today’s digital age. Seeking professional help can significantly enhance your data security. Experts in cybersecurity and specialized data protection services can provide robust solutions. This section focuses on how consulting with cybersecurity experts and utilizing data protection services can keep your information safe.
Consulting With Cybersecurity Experts
Cybersecurity experts offer specialized knowledge to safeguard your online data. They can identify vulnerabilities in your system and provide tailored solutions. Here are some benefits:
- Risk Assessment: Experts conduct thorough assessments to find potential threats.
- Custom Solutions: They design security measures based on your specific needs.
- 24/7 Monitoring: Continuous monitoring of your systems helps detect and prevent breaches.
- Training: They offer training sessions to educate you on best practices for data security.
Consulting with cybersecurity experts ensures a comprehensive approach to data protection. Their expertise covers various aspects, from software updates to network security. Below is a table summarizing the key services provided by cybersecurity experts:
| Service | Description |
|---|---|
| Vulnerability Assessment | Identifies weaknesses in your systems |
| Penetration Testing | Simulates attacks to test your defenses |
| Incident Response | Provides immediate action during a breach |
| Security Audits | Evaluates your current security measures |
Utilizing Data Protection Services
Data protection services are crucial for maintaining the privacy and integrity of your information. These services offer various tools and solutions to keep your data safe. Here are some advantages:
- Encryption: Protects your data by converting it into unreadable code.
- Backup Solutions: Regular backups ensure your data is not lost.
- Access Controls: Limits who can view or use your data.
- Data Masking: Hides sensitive information from unauthorized access.
Utilizing these services adds an extra layer of security to your data. They can protect against various threats, including hacking, phishing, and malware attacks. The table below outlines some key data protection services:
| Service | Description |
|---|---|
| Data Encryption | Transforms data into a secure format |
| Cloud Backup | Stores data securely in the cloud |
| Access Management | Controls data access permissions |
| Data Masking | Conceals sensitive information |
By integrating these services, you can ensure your personal data remains secure and private.

Credit: www.researchgate.net
Frequently Asked Questions
How To Protect Your Personal Data On The Internet?
Use strong, unique passwords for all accounts. Enable two-factor authentication. Regularly update software and apps. Avoid sharing personal information on social media. Use a VPN for secure internet connections.
How Can I Protect Myself On The Internet Online?
Use strong passwords and update them regularly. Enable two-factor authentication. Avoid clicking on suspicious links. Keep software and antivirus updated. Use secure, private networks.
How Can I Manage My Personal Data Online?
Manage personal data online by using strong passwords. Enable two-factor authentication. Regularly update software. Limit data sharing on social media. Use secure, trusted websites.
Is It Possible To Protect Your Privacy Online?
Yes, it is possible to protect your privacy online. Use strong passwords, enable two-factor authentication, and avoid sharing personal information. Regularly update software and use VPNs for secure browsing. Be cautious of phishing scams and review privacy settings on social media.
How Can I Secure My Online Accounts?
Use strong, unique passwords and enable two-factor authentication to protect your online accounts from unauthorized access.
What Are The Best Privacy Settings?
Adjust privacy settings on social media and apps to limit data sharing. Review and update them regularly for optimal security.
Conclusion
Safeguarding your personal data online is crucial. Implement strong passwords and utilize two-factor authentication. Stay vigilant against phishing scams and update your software regularly. Educate yourself on privacy settings and use secure networks. By following these steps, you can significantly enhance your online security and protect your valuable information.
